January 10, 2024, written by
Andrii Minchekov
Identity management is a critical component of modern IT infrastructure, enabling organizations to manage the identities and access of internal users such as employees, contractors, partners, and consumers as well. This article explores the concept of identity management, its benefits for business owners, and how to integrate Microsoft Azure Active Directory (AAD) and Microsoft Graph API to get access to custom business applications or standard corporate apps like Microsoft Office 365, SharePoint, OneDrive, Outlook Mail, Calendar, etc.
Identity management involves handling the identities of users. This includes managing access to corporate resources, applications, and services. Effective identity management ensures that only authorized users have access to the right resources at the right times for the right reasons.
A large enterprise might use Microsoft Azure Active Directory to manage employee access to various corporate applications like Office 365, SharePoint, OneDrive, Outlook Mail, Calendar, and internal HR systems. Employees use their organizational credentials to log in to all required applications via SSO.
Integrating identity management with Microsoft Azure Active Directory (AAD) offers several benefits for business owners:
This section demonstrates how to build a Spring Boot Web MVC application that provides API endpoints integrated with Microsoft Azure Active Directory for managing organizational identities. The application implements the "Resource Owner Password Credentials (ROPC) Authentication" scheme in Active Directory, leveraging Microsoft Graph APIs. This scheme is suitable for scenarios where a custom registration and authentication process with a tailored UI/UX is a business requirement for your organization.
Checkout my Github repository to see the source code of the Spring Boot Web MVC app with AAD Integration and Microsoft Graph API usage.
Sign in to Azure and connect to the Azure AD tenant where you would like to manage users.
On the left menu, select App registrations.
Click + New Registration.
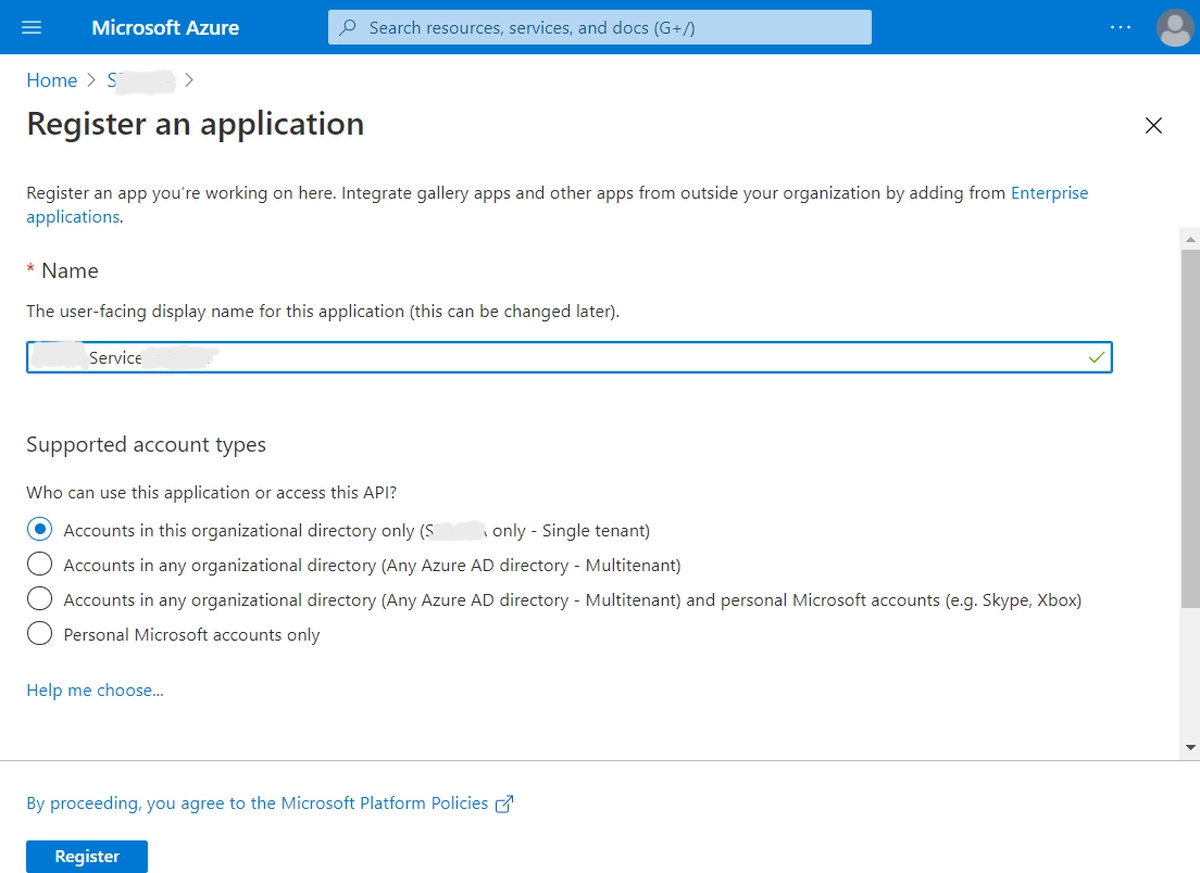
Under Name, enter a unique application name.
Under Supported account types, select Accounts in this organizational directory only.
Click Register.
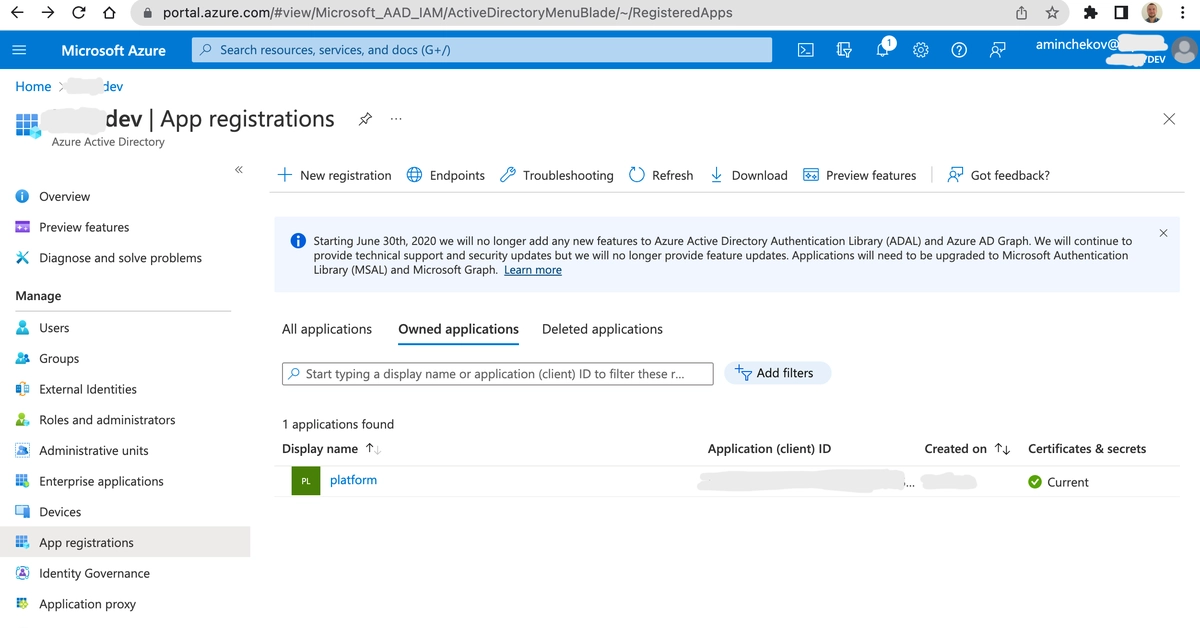
Select the new registered app from the list of App Registrations.
Select Certificates & secrets from the left menu.
Click + New Client Secret.
Provide a Description and appropriate Expiry. If you select 1 or 2 years, the service principal must be refreshed with a new client secret on the anniversary of its creation.
Click Add.
Create a copy of the client secret and store it in a safe place. This is the only time it is displayed. This is needed to add the account to the Vault.
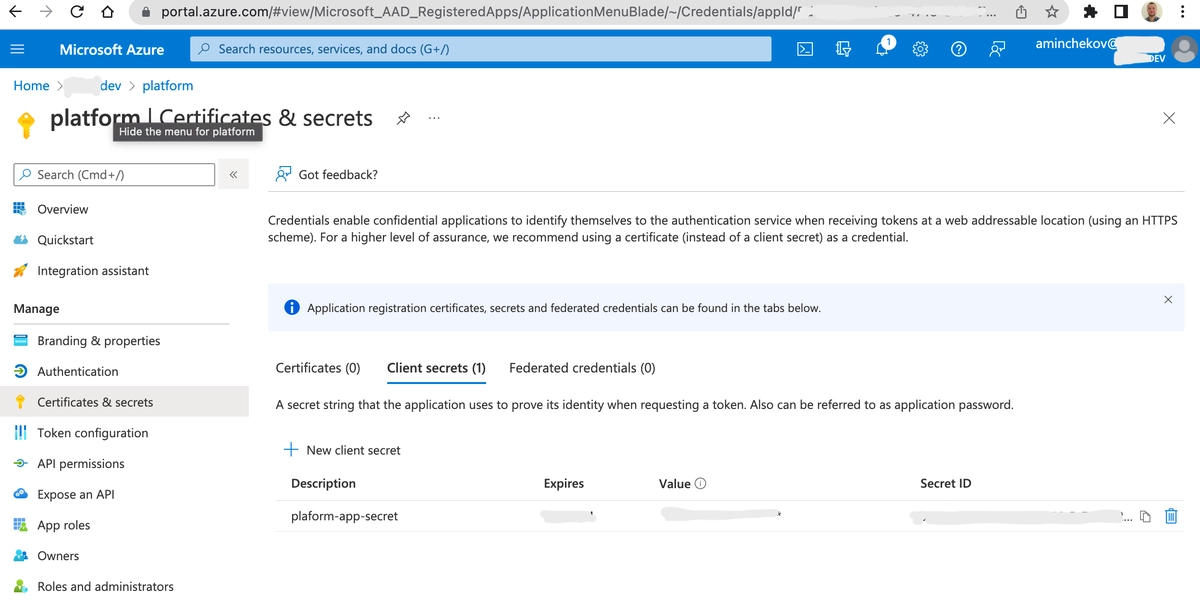
Assign API Permissions to the Registered Core Service (platform) App.
Search Azure for Azure AD roles and administrators.
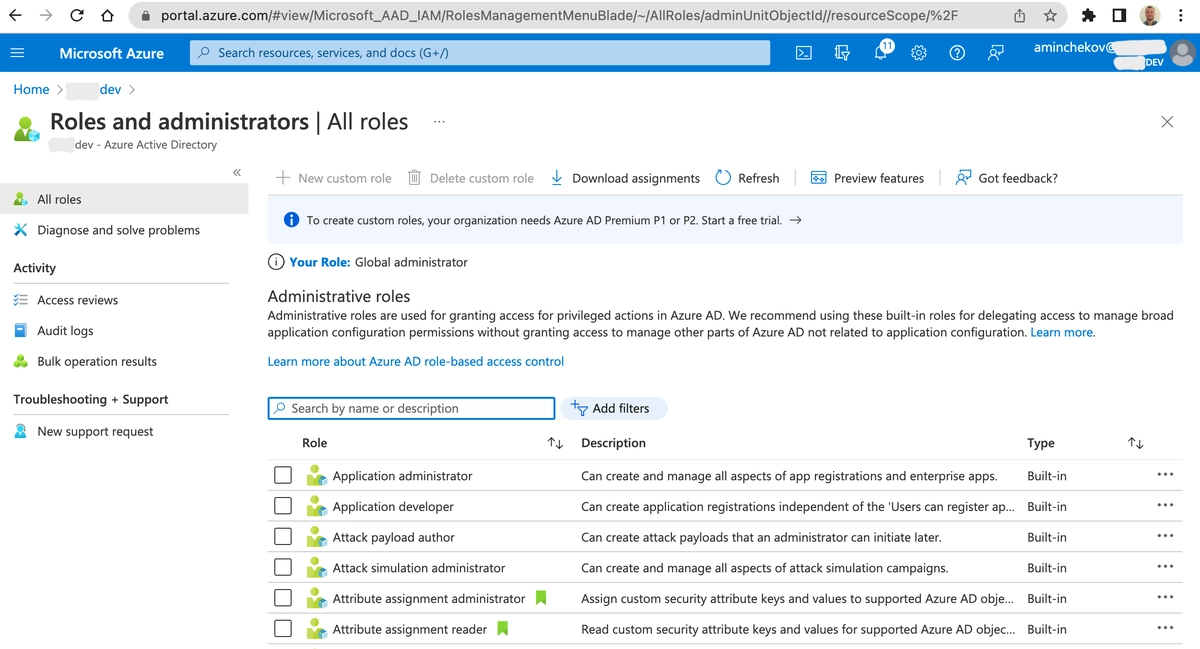
Search for the role User Administrator. The User Administrator role gives the application sufficient permissions to change most passwords, with the exception of Authentication Admin, Global Admin, Privileged Authentication Admin, and Privileged Role Admin.
Click the Role or the ellipsis button for the role and then click Description.
On the left menu, click Assignments (if not already selected).
Click + Add assignments.
In the Search box, type the name of the registered app that was created earlier. Registered apps are not listed with users and can only be found this way.
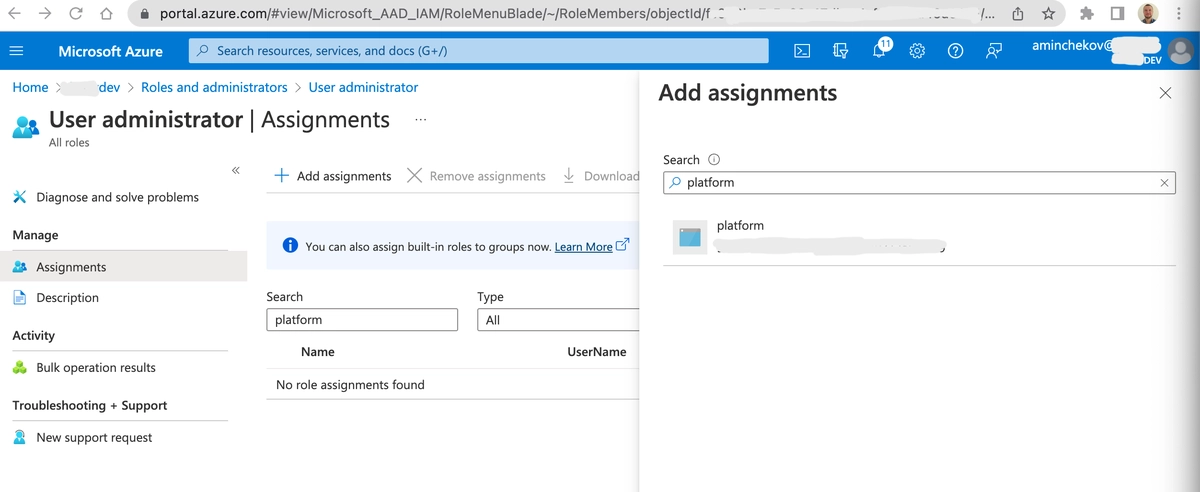
The previously created registered app is visible in the search results. Select it and click Add. Service Principal assignment is done, thus the application will have enough rights to use Graph API to create users and change user passwords in Active Directory.
A company with 500 employees needs to manage access to internal applications and services. It uses Azure AD and Microsoft Graph API to:
Integrating Microsoft Azure Active Directory for identity management provides significant benefits for business owners, including enhanced security, simplified user management, and improved user experience. By following the steps outlined in this article, you can configure Azure AD and leverage its capabilities to manage user identities effectively.